Arwentech Cyber Security for better protection
Cyber Security
Home > Cyber Security
Arwen Tech is a leading provider of cyber and network security solutions for businesses of all sizes i.e. Enterprises, SMB, SMEs etc. and of all sectors i.e. financial, corporate, technology and power sector. With more than 20 years of experience in the industry, we have developed a deep understanding of the threats and challenges facing modern networks, and we have built a suite of products and services to address them. Our network security solutions are designed to protect against a wide range of threats, including hacking, malware, phishing attacks, and more. We use the latest technologies and techniques to ensure that our clients’ networks are secure and that their data is protected at all times. We provide specialized services for the following domains:

Cyber Security
In the evolving digital landscape cyber security is a critical factor for all types of originations irrespective of their size and nature of services. As organizations rely on digital infrastructure today for operations, threat landscape has expanded, making them more vulnerable for cyber-attacks. Cyber threats have evolved in both complexity and frequency, targeting businesses of all sizes and across all sectors. Cyber security is critical for secure digital assets and to meet the compliance requirements.
Read More
Understanding these needs Arwen Tech is committed to provide cyber security services backed by teams of experts in the domains of Security Operations, Security Assessments, Security Testing, Security Solutions and Security Consultancy. Arwen Tech Team is committed to delivering expertise, innovation, and dedication in tackling the challenges of the modern cyber threat landscape.
The multidimensional team is structured to deliver a wide range of services including security monitoring, incident response, vulnerability management, threat intelligence, security assessments, governance planning and regulatory compliance. These services will be tailored to meet the unique needs of each client, ensuring a personalized approach to cybersecurity that is both effective and efficient.







Security Consultancy
Cyber Security Consultancy services at Arwen Tech offer comprehensive support lead by a team of experts to design, implement, and optimize security measures based on client’s specific need. Provide clients best solutions and expert opinions based on industry standards to protect their digital assets and fulfill their regulatory requirements.
Read More
- Security Design:
Our Security Design services focus on creating a strong foundation for security infrastructure. It involves identifying the current security posture, meet client expectations, and provide best solutions to fit in with existing security infrastructure. This includes network design, data protection strategies, access control measures, and more.
- Security Solutions:
Arwen Tech offers consultancy services to evaluate customer requirements and define Security Solutions to address client’s requirements and challenges. This includes recommendations and implementation of advanced security technologies such as SIEM, SOAR, DLP, PAM, IAM, IGA, EDR/XDR, NDR MFA, ZTNA and database security. We ensure that these solutions are seamlessly integrated into your existing IT environment to provide maximum protection with minimal disruption.
- Security implementation:
Security Implementation services ensure the effective deployment, implementation and testing of security solution considering the client’s requirements and industry best standards. The aim is to provide end-to-end implementation support, including configuration, testing, and validation of security technologies. Arwen tech team is committed to work closely with client’s security and IT staff to ensure a smooth transition and to train them on security solutions.
- DevSecOps implementation
DevSecOps services ensure the effective and seamless integration with software development lifecycle to identify and mitigate security risk before the manifest in production environment. Arwen Tech provides guidance on secure coding practices, continuous security testing, vulnerability management and automated security checks to ensure that client’s applications are secure from development to deployment.
- Security Optimization:
Security Optimization services focus on enhancing the performance and effectiveness of client’s existing security solutions and policies. Arwen Tech team helps client’s conduct regular assessments and audits to identify areas for improvement and provide recommendations to optimize the security infrastructure and solutions. The goal is to ensure that the security measures in client’s IT infrastructure are up-to-date and capable of defending against emerging threats.

Managed Security Operations


Perimeter Security
Read More
- Email Security
- Next Generation Firewalls
- Web Application Firewalls
- Anti-DDoS





Identity and Access
Read More
- Privilege Access Management (PAM)
- Identity and Access Management (IAM)
- Identity, Governance and Administration (IGA)
- Mobile Device Management
- Zero Trust Network Access (ZTNA)
- Multifactor Authentication



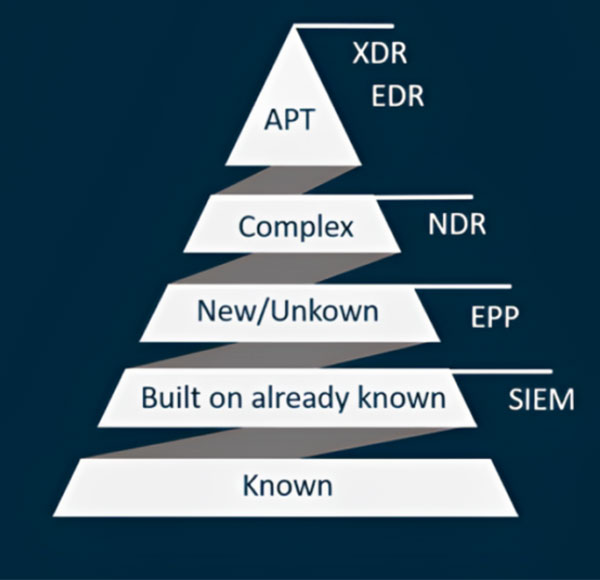
Detection and Response
Read More
- End Point Detection and Response (EDR)
- Extended Detection and Response (XDR)
- Network Detection and Response (NDR)
- Security Information and Event Management (SIEM)
- Security Orchestration and Automated Response (SOAR)

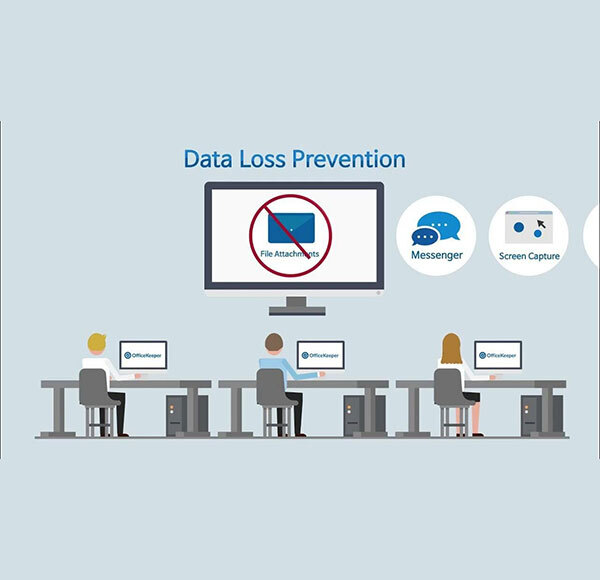
Data Protection
Read More
- Data Loss Prevention (DLP)
- Data Classification
- Database Protection and Analytics





Application Security
Read More
- The type of data that you need to protect: DLP solutions can be used to protect a wide range of data, including sensitive customer data, intellectual property, and financial data. It is important to choose a solution that can protect the specific types of data that you need to protect.
- The level of security that you require: DLP solutions offer a variety of security features. It is important to choose a solution that offers the level of security that you require.
- The ease of use: DLP solutions can be complex to implement and manage. It is important to choose a solution that is easy to use and that can be managed by your existing IT staff.
By choosing the right DLP solution, you can help to protect your organization from data breaches.
Here are some of the benefits of using a DLP solution:
- Reduced risk of data breaches: DLP solutions can help to reduce the risk of data breaches by detecting and preventing unauthorized access to sensitive data.
- Improved compliance: DLP solutions can help organizations to comply with regulations, such as HIPAA and PCI DSS.
- Increased efficiency: DLP solutions can help organizations to improve efficiency by automating data protection tasks.
- Reduced costs: DLP solutions can help organizations to reduce costs by eliminating the need for manual data protection tasks.
If you are an organization that is looking for a way to protect your sensitive data, then you should consider using a DLP solution. These solutions can help you to detect and prevent data breaches, which can help you to protect your organization’s reputation and bottom line.
By partnering with Arwen Tech for their data leak prevention needs, businesses can ensure that their sensitive data is protected at all times, and that they are complying with regulatory requirements and industry best practices. Contact us today to learn more about our data leak prevention solutions and how we can help your business stay secure.


Cloud Security
Risk-based Financial Fraud Management Solution is a comprehensive solution that helps financial institutions to detect and prevent fraud. The solution combines a variety of technologies, including artificial intelligence, machine learning, and big data analytics, to provide a holistic view of fraud risk. This allows financial institutions to identify and prioritize risks, and to implement appropriate mitigation measures.
Read More
The Risk-based Financial Fraud Management Solution includes the following features:
- Fraud detection: The solution uses a variety of techniques to detect fraud, including machine learning, big data analytics, and artificial intelligence. This allows the solution to identify even the most sophisticated fraud attempts.
- Fraud prevention: The solution provides a variety of tools to help financial institutions prevent fraud, including risk scoring, transaction monitoring, and anomaly detection. This helps financial institutions to stop fraud before it happens.
- Fraud investigation: The solution provides tools to help financial institutions investigate fraud, including case management, evidence collection, and reporting. This helps financial institutions to identify and prosecute fraudsters.
Arwentech proudly offers Risk-based Financial Fraud Management Solution that is a powerful tool can help financial institutions to protect themselves from fraud. These solutions are easy to use and scalable, and it can be customized to meet the specific needs of each financial institution.
Here are some of the benefits of using Risk-based Financial Fraud Management Solution:
- Reduced fraud losses: The solution can help financial institutions to reduce fraud losses by up to 50%.
- Improved customer experience: The solution can help financial institutions to improve the customer experience by reducing the number of false positives.
- Increased compliance: The solution can help financial institutions to comply with regulations, such as PSD2 and GDPR.
- Reduced operational costs: The solution can help financial institutions to reduce operational costs by automating fraud detection and prevention processes.
If you are a financial institution, then you should consider using Risk-based Financial Fraud Management Solution to protect yourself from fraud. The solution is a powerful tool that can help you to reduce fraud losses, improve the customer experience, increase compliance, and reduce operational costs.

Threat Intelligence
Application security is a critical part of any organization’s overall security strategy. It is the process of protecting applications from unauthorized access, modification, or destruction.
Synopsys is a leading provider of application security solutions. Its solutions help organizations to identify, fix, and protect against vulnerabilities in their applications.
Synopsys offers a wide range of application security solutions, including:
Read More
- Static application security testing (SAST): SAST tools scan application code for potential security vulnerabilities.
- Dynamic application security testing (DAST): DAST tools simulate attacks on applications to identify security vulnerabilities.
- Interactive application security testing (IAST): IAST tools combine SAST and DAST to provide a more comprehensive view of application security.
- Software composition analysis (SCA): SCA tools scan application dependencies for known vulnerabilities.
- Penetration testing: Penetration testing is a simulated attack on an application to identify security vulnerabilities.
- Security code review: Security code reviews are performed by human analysts to identify security vulnerabilities.
- Security education and training: Security education and training help developers and other employees to understand security best practices.
Synopsys’ application security solutions are used by organizations of all sizes in a wide range of industries, including financial services, healthcare, and government. Synopsys’ solutions help organizations to protect their applications from a variety of threats, including data breaches, malware attacks, and insider threats.
Contact us today to learn more about Application Security Solutions and how we can help your business stay secure.



Managed Security Operations
- Managed Security Operations
Through managed security operation services we offer continuous monitoring, incident response, and threat analysis to deliver end-to-end cyber security operations. Responsible for establishing clear communication channels with clients to understand their security needs and pain points. Managed SOC Services are divided into three levels, ensuring that we provide the appropriate response and expertise at each stage of an incident. These services will be tailored to clients’ specific needs, offering SOC L1, L2, or L3 support based on their individual requirements. The SOC team will manage, monitor, and respond utilizing solutions such as SIEM, SOAR, EDR, XDR, EPP, and firewalls, whether they are installed and configured on client premises, or on cloud.
Read More
- Managed SOC
Our Managed Security Operations Centre (SOC) offers comprehensive, around-the-clock monitoring and threat detection and response services to safeguard our client’s assets. Our SOC team leverage’s best practices to ensure your organization’s data remains secure. Following are the service afford within managed SOC.
- SOC L1 Services:
Continuous Monitoring (24/7): Provide continuous monitoring of security events and alerts using security information and event management (SIEM) systems.
Initial Incident Triage: Conduct the initial triage of security incidents to determine the severity and urgency of threats.
Basic Threat Analysis: Perform basic analysis of security events to identify potential threats and vulnerabilities.
- SOC L2 Services:
In-depth Incident Analysis: Conduct detailed analysis of security incidents to understand the root cause and impact of threats.
Incident Response Coordination: Coordinate with relevant stakeholders to ensure timely and effective response to security incidents.
Threat Containment and Mitigation: Implement containment and mitigation strategies to minimize the impact of security incidents.
- SOC L3 Services:
Advanced Threat Analysis: Perform advanced threat analysis and digital forensics to identify root causes and threat actors.
Proactive Threat Hunting: Perform proactive threat hunting activities to identify and mitigate potential threats before they materialize.
Threat Intelligence: Gather Threat Intelligence feeds, and perform solution enrichment, to stay updated and manage a pro active defence.
Security Advisory: Provide expert security advisory services to help clients strengthen their overall security posture.
Threat Actor Profiling: Profile threat actors to understand their tactics, techniques, and procedures (TTPs).
- Digital Forensics and Incident Response (DFIR)
We use advanced tools and methodologies to quickly identify the scope and impact of the incidents, limiting its spread and reducing potential damage. We provide following services as per the industry best practices and procedures.
- In-Depth Forensic Analysis
- Manual and Automated Incident Response
- Comprehensive Reporting
- Remediations and Recommendations
- Compromise Assessments
Through proactive compromise assessment we evaluate your network and assist to identify signs of malicious activities that may have gone undetected. Compromise Assessment gives you confidence that your IT environment is secure. we provide actionable recommendations to enhance your security posture. Our goal is to help you address vulnerabilities and implement measures to prevent future compromises.
- Threat Hunting

Managed Security Services
We provide complete management of security solutions to safeguard your digital assets and ensure business continuity. Our team continuously configures, monitors, and optimizes bellow mentioned solutions based on industry best practices to ensure they deliver maximum protection for your organization.
- Managed SIEM
- Managed SOAR
- Managed EDR
- Managed XDR
Managed Identity and Access
Read More
- Static application security testing (SAST): SAST tools scan application code for potential security vulnerabilities.
- Dynamic application security testing (DAST): DAST tools simulate attacks on applications to identify security vulnerabilities.
- Interactive application security testing (IAST): IAST tools combine SAST and DAST to provide a more comprehensive view of application security.
- Software composition analysis (SCA): SCA tools scan application dependencies for known vulnerabilities.
- Penetration testing: Penetration testing is a simulated attack on an application to identify security vulnerabilities.
- Security code review: Security code reviews are performed by human analysts to identify security vulnerabilities.
- Security education and training: Security education and training help developers and other employees to understand security best practices.
Synopsys’ application security solutions are used by organizations of all sizes in a wide range of industries, including financial services, healthcare, and government. Synopsys’ solutions help organizations to protect their applications from a variety of threats, including data breaches, malware attacks, and insider threats.
Contact us today to learn more about Application Security Solutions and how we can help your business stay secure.



Security Operations Center (SOCaaS) as a service
- Coming Soon
Read More
- Managed SOC
Our Managed Security Operations Centre (SOC) offers comprehensive, around-the-clock monitoring and threat detection and response services to safeguard our client’s assets. Our SOC team leverage’s best practices to ensure your organization’s data remains secure. Following are the service afford within managed SOC.
- SOC L1 Services:
Continuous Monitoring (24/7): Provide continuous monitoring of security events and alerts using security information and event management (SIEM) systems.
Initial Incident Triage: Conduct the initial triage of security incidents to determine the severity and urgency of threats.
Basic Threat Analysis: Perform basic analysis of security events to identify potential threats and vulnerabilities.
- SOC L2 Services:
In-depth Incident Analysis: Conduct detailed analysis of security incidents to understand the root cause and impact of threats.
Incident Response Coordination: Coordinate with relevant stakeholders to ensure timely and effective response to security incidents.
Threat Containment and Mitigation: Implement containment and mitigation strategies to minimize the impact of security incidents.
- SOC L3 Services:
Advanced Threat Analysis: Perform advanced threat analysis and digital forensics to identify root causes and threat actors.
Proactive Threat Hunting: Perform proactive threat hunting activities to identify and mitigate potential threats before they materialize.
Threat Intelligence: Gather Threat Intelligence feeds, and perform solution enrichment, to stay updated and manage a pro active defence.
Security Advisory: Provide expert security advisory services to help clients strengthen their overall security posture.
Threat Actor Profiling: Profile threat actors to understand their tactics, techniques, and procedures (TTPs).
- Digital Forensics and Incident Response (DFIR)
We use advanced tools and methodologies to quickly identify the scope and impact of the incidents, limiting its spread and reducing potential damage. We provide following services as per the industry best practices and procedures.
- In-Depth Forensic Analysis
- Manual and Automated Incident Response
- Comprehensive Reporting
- Remediations and Recommendations
- Compromise Assessments
Through proactive compromise assessment we evaluate your network and assist to identify signs of malicious activities that may have gone undetected. Compromise Assessment gives you confidence that your IT environment is secure. we provide actionable recommendations to enhance your security posture. Our goal is to help you address vulnerabilities and implement measures to prevent future compromises.
- Threat Hunting

Security Assessments
As part of pre and post deployment approach in cyber security, security assessments play a vital role in enhancing and optimization of cyber security controls and configurations. We offer assessment services in line with industry best practices and standards i.e. ISO27000, NIST CSF and 800-53, CIS, HIPAA, HiTrust, SOC2, GDPR
Read More
- SOC Maturity Assessment
The purpose of SOC Maturity Assessment is to assess the current state of SOC and find out gaps between current and desired maturity and capability state. This exercise provides precise recommendations and milestones to achieve the desired state. This assessment is performed based on Capability and Maturity Model Integration (CMMI), NIST CSF, ISO 27001 standard and industry best practices.
It evaluates and improve the effectiveness, efficiency, and readiness of the SOC in defending against cybersecurity threats and responding to security incidents. This assessment aims to provide a comprehensive understanding of the SOC’s current state and its alignment with industry best practices and organizational goals.
- Cyber Security Maturity Assessment
The aim of cyber security maturity evaluation is a comprehensive review of the organization’s cybersecurity posture, assessing the effectiveness of security controls, policies, and procedures. It also quantifies and provides actionable steps to achieve a desired cyber security posture. This Cyber model consists of five levels or stages that represent the degree of sophistication and effectiveness of your cybersecurity processes, controls, and outcomes. This assessment helps organizations understand their current cybersecurity maturity level and provides recommendations for industry best practices.
- OT security Maturity Assessment
OT security maturity assessment aims to provide organizations with a clear understanding of their current OT security posture, identify areas for improvement, and develop a roadmap to enhance resilience against cyber threats targeting industrial control systems and critical infrastructure. This assessment is performed based on Cybersecurity Capability Maturity Model (C2M2) and NIST CSF. It uses a set of industry-vetted cybersecurity practices focused on both information technology (IT) and operations technology (OT) assets and environments.
- DevSecOps Maturity Assessment
DevSecOps maturity Assessment Evaluates the integration of security practices within the DevOps pipeline. This assessment examines the maturity of security measures throughout the software development lifecycle, ensuring that security is embedded in development, deployment, and operations processes. This assessment is performed based on four maturity models to evaluate the current state of security measures from development, testing, integration, till the deployment and provides actions to be taken to achieve the desired maturity level.
- Compromise assessment
Compromise assessment is a thorough investigation to determine if the organization’s systems and networks have been compromised by malicious actors. This assessment involves examining logs, system artifacts, and network traffic to identify indicators of compromise and provide recommendations for remediation.


Security Testing
Security testing has become very critical considering a proactive approach to assess organization’s security. We offer services for focused testing on specific areas and identify gaps to quantify the efforts required to strengthen security.
Read More
- Blackbox External Penetration Testing
This testing is conducted from the perspective of an external attacker with no prior knowledge of the internal systems.
This approach simulates real-world attack scenarios to identify vulnerabilities that could be exploited from outside the organization’s network. This ensures all the aspects of an application or network infrastructure are secure including all input and output points in data flow stream.
- Grey Box Internal Penetration Testing
Grey Box Testing is a hybrid approach that combines aspects of both Black Box Testing and White Box Testing. It involves testing software with partial knowledge of its internal workings. Testers have access to some information about the software’s architecture, design, and code, which allows for more effective and targeted testing.
- Targeted Penetration Testing
Targeted penetration testing focuses on specific areas of a system or application that are deemed critical or high-risk. This type of testing is usually directed by the client or based on a threat model. The scope is predefined and limited to particular components, functionalities, or assets of interest. It is performed with minimal internal knowledge of application or function of an application.
- Code Assisted Penetration Testing
Code Assisted Penetration Testing is a detailed targeted security assessment process that combines traditional penetration testing methods with in-depth code analysis. This approach allows for the identification of vulnerabilities within the application code that may not be visible through black-box testing alone. It usually includes a hybrid of automated runtime scanning and manual testing based on the application nature and source code.
- Network Infrastructure Penetration Testing
This type of penetration testing conducted to evaluate the network infrastructure behavior and operations under various conditions considering confidentiality, Integrity and availability of digital assets. Penetration tester mimics an attacker to simulate real world attacks to test the security controls and procedures. This testing could be conducted either from the perspective of internal user (white box or grey box penetration testing) or as external attacker (Black Box penetration testing)
- Web Application Penetration Testing
These tests are conducted to validate the functionality and security of a web application. It Includes testing of user interfaces, 3rd party integrations, APIs, plugins, and backend services. This testing could be conducted either from the perspective of internal user (white box or grey box penetration testing) or as external attacker (black Box penetration testing).
- Mobile Application Penetration Testing
Mobile application penetration testing involves evaluating the security of mobile applications running on mobile devices like smartphones and tablets. This includes testing both iOS and Android platforms. It focuses on the security of the mobile app installed on the device, including local storage, communication, and app permissions. This testing could be conducted either from the perspective of internal user (white box or grey box penetration testing) or as an external attacker (black Box penetration testing).
- AI Assisted Penetration Testing
AI-Assisted penetration testing involves the use of artificial intelligence and machine learning techniques to develop malwares or to enhance the effectiveness testing processes. Using AI penetration tester automates repetitive tasks, such as scanning for vulnerabilities, reducing the time and effort required for manual testing. AI models learn from the behaviour of applications and improve their ability to detect vulnerabilities.
- OT Penetration Testing
OT (Operational Technology) penetration testing ensures the security and reliability of systems controlling critical infrastructure and Identifies vulnerabilities that could be exploited by malicious actors to change, disrupt, physical damage, or affect industrial system in any way. This testing focuses on the security testing of industrial control systems (ICS), SCADA systems (Supervisory Control and Data Acquisition), PLCs (Programmable Logic Controllers), and other industrial devices.
- IoT Penetration Testing
IoT penetration Testing ensures the security and integrity of interconnected devices and systems and identifies vulnerability that could lead to information leakage or unauthorized access. This penetration testing evaluates the security of smart devices, sensors, communication protocols, and associated software.

Governance, Risk and Compliance
Governance, Risk, and Compliance (GRC) services integrate Governance, Risk management, and Compliance into business operations. They ensure that policies are followed, risks are managed, and regulatory requirements are met through continuous monitoring. Our expert team can build, operate and optimize the complete process considering the Regulatory compliances i.e. ISO27000, NIST CSF and 800-53, CIS, HIPAA, HiTrust, SOC2, GDPR.
Read More
- Governance framework
To ensure effective oversight, accountability, and decision-making processes, compliance management within the organization.
- Design and implementation
Comprehensive regulatory compliance programs to meet specific industry standards and regulations.
- Risk assessments
Identify and evaluate potential risks to the organization’s assets and operations. Development and implementation of risk treatment plans based on organization’s risk appetite.
- Policies and Procedures
Creation and implementation of security policies and procedures based on regulatory compliances.
- Security Audits
To assess the effectiveness of the organization’s security controls, policies, and procedures. These audits help identify areas of non-compliance and meet requirements for the regulatory compliance and standards.




DevSecOps
The DevSecOps approach includes incorporating security as a significant component of DevOps practices. DevSecOps services provide continuous monitoring. Assessment and correction with respect to complete development life cycle which ultimately ensures that loopholes and weaknesses are identified early in the development process and remediated immediately.
Following are service offerings for DevSecOps implementation:
- Establishing, implementing and managing a robust vulnerability management program to continually identify, assess, and remediate vulnerabilities in the organization’s systems and applications.
- Implement security measures to protect containerized applications and environments including docker and kubernetes etc. This includes securing container images, managing container runtime security, and implementing security controls within the container orchestration platform.
- Installation and deployment of application security solutions to Integrate security practices into the software development lifecycle to ensure the security of applications. This includes Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST)
- Deploy and manage Public Key Infrastructure (PKI) solutions to ensure secure communication and authentication within the organization.
Integrate security checks into the Continuous Integration and Continuous Deployment (CI/CD) pipeline to identify and address security issues early in the development process.
Read More
- Grey Box Internal Penetration Testing
Grey Box Testing is a hybrid approach that combines aspects of both Black Box Testing and White Box Testing. It involves testing software with partial knowledge of its internal workings. Testers have access to some information about the software’s architecture, design, and code, which allows for more effective and targeted testing.
- Targeted Penetration Testing
Targeted penetration testing focuses on specific areas of a system or application that are deemed critical or high-risk. This type of testing is usually directed by the client or based on a threat model. The scope is predefined and limited to particular components, functionalities, or assets of interest. It is performed with minimal internal knowledge of application or function of an application.
- Code Assisted Penetration Testing
Code Assisted Penetration Testing is a detailed targeted security assessment process that combines traditional penetration testing methods with in-depth code analysis. This approach allows for the identification of vulnerabilities within the application code that may not be visible through black-box testing alone. It usually includes a hybrid of automated runtime scanning and manual testing based on the application nature and source code.
- Network Infrastructure Penetration Testing
This type of penetration testing conducted to evaluate the network infrastructure behavior and operations under various conditions considering confidentiality, Integrity and availability of digital assets. Penetration tester mimics an attacker to simulate real world attacks to test the security controls and procedures. This testing could be conducted either from the perspective of internal user (white box or grey box penetration testing) or as external attacker (Black Box penetration testing)
- Web Application Penetration Testing
These tests are conducted to validate the functionality and security of a web application. It Includes testing of user interfaces, 3rd party integrations, APIs, plugins, and backend services. This testing could be conducted either from the perspective of internal user (white box or grey box penetration testing) or as external attacker (black Box penetration testing).
- Mobile Application Penetration Testing
Mobile application penetration testing involves evaluating the security of mobile applications running on mobile devices like smartphones and tablets. This includes testing both iOS and Android platforms. It focuses on the security of the mobile app installed on the device, including local storage, communication, and app permissions. This testing could be conducted either from the perspective of internal user (white box or grey box penetration testing) or as an external attacker (black Box penetration testing).
- AI Assisted Penetration Testing
AI-Assisted penetration testing involves the use of artificial intelligence and machine learning techniques to develop malwares or to enhance the effectiveness testing processes. Using AI penetration tester automates repetitive tasks, such as scanning for vulnerabilities, reducing the time and effort required for manual testing. AI models learn from the behaviour of applications and improve their ability to detect vulnerabilities.
- OT Penetration Testing
OT (Operational Technology) penetration testing ensures the security and reliability of systems controlling critical infrastructure and Identifies vulnerabilities that could be exploited by malicious actors to change, disrupt, physical damage, or affect industrial system in any way. This testing focuses on the security testing of industrial control systems (ICS), SCADA systems (Supervisory Control and Data Acquisition), PLCs (Programmable Logic Controllers), and other industrial devices.
- IoT Penetration Testing
IoT penetration Testing ensures the security and integrity of interconnected devices and systems and identifies vulnerability that could lead to information leakage or unauthorized access. This penetration testing evaluates the security of smart devices, sensors, communication protocols, and associated software.


Social Media Security
Application security is a critical part of any organization’s overall security strategy. It is the process of protecting applications from unauthorized access, modification, or destruction.
Synopsys is a leading provider of application security solutions. Its solutions help organizations to identify, fix, and protect against vulnerabilities in their applications.
Synopsys offers a wide range of application security solutions, including:
Synopsys’ application security solutions are used by organizations of all sizes in a wide range of industries, including financial services, healthcare, and government. Synopsys’ solutions help organizations to protect their applications from a variety of threats, including data breaches, malware attacks, and insider threats.
Contact us today to learn more about Application Security Solutions and how we can help your business stay secure.